Editor’s note: This article is the second of a two-part series on human trafficking detection, typologies and methodology. It first appeared on the ACAMS Today website.
The first part of this series, “Human Trafficking: Persona-based Typologies and Methodology,”1 re-emphasized the scale of the human trafficking (HT) problem and the key investigation challenges to tackle, including the need to reconsider the current human trafficking detection and investigation approach.
This article further details the use of a persona-based approach in conducting human trafficking detection and investigations and also provides examples of how it can be applied to disrupt HT more effectively.
Persona-Based Approach for Human Trafficking Detection
As explained in the first part of this series, persona-based detection models can be an effective alternative to current rule-based detection models. This approach allows the identification of suspicious activity in financial data by looking for patterns in customer behavior indicative of HT.
Persona-based typologies refer to a method of categorizing and understanding the different types of people, organizations and their characteristics in the context of specific financial crime types. It involves using a combination of financial data analysis and investigative techniques to identify the financial activities of traffickers, their victims and associated networks.
This approach focuses on the specific traits and behaviors of individual criminals and networks rather than solely analyzing the criminal activities themselves, avoiding duplication. Persona-based typologies can be further used to identify vulnerable individuals that may be at a higher HT risk. Lastly, this approach also enables effective comparison against similar customer profiles, as well as analysis against known “guilty party” data.
Step 1: Identifying Target HT Typologies
HT typologies and business models are complex, diverse and ever-evolving. These crimes involve a variety of different roles, actors and entities. Therefore, understanding and accounting for the different types of HT and identifying the unique personas that make up criminals, their victims and the specific ways in which they operate is crucial to better target the efforts to prevent and combat these crimes.
To determine which HT typologies and personas are relevant for you, first, you need to assess your exposure:
- Where do you operate? Do you operate regionally only, nationally or internationally? A broader geographical scope means higher and more diverse HT risk.
- Who are your customers? Businesses only, individuals only or all types, big and small—where are they located, what do they do and what is your tolerance for high-risk HT customers?
- What are your products and channels? Do you offer credit cards, have high-street branches and/or onboard new customers remotely? Some product and channel types are more vulnerable to HT.
Different types of banks have different vulnerabilities. For example, if your customer base is business-only, there is little use in trying to detect an individual trafficker. And vice versa—looking for commercial-front brothel red flags in a retail-only bank’s data is futile.
Once you understand your exposure, you can start to model the profiles of personas participating in these crimes. Think about the crime in your area of operation. Which actors are likely to be involved that might be your customers? Another aspect to consider is the additional actors that you might frequently see that look similar and could be involved in these crimes. These may represent criminal, victim or other legitimate personas. If you can model and anticipate these, you can remove legitimate actors from your data and assess connectivity to other crimes.
Step 2: Defining Your Model
In this context, a model is a way to represent the personas that are potentially connected to the HT risks you face. It is a practical foundation for any HT investigation, allowing knowledge to be structured and gaps to be understood and addressed.
To illustrate how to define a model, this article uses a commercial-front brothel typology2 as an example. This typology targets behaviors of businesses with legal fronts that are facilitating commercial sex trafficking on their premises. To conceal their criminal activity, these businesses use seemingly legitimate storefronts but function primarily as brothels, known as commercial-front brothels. Although these businesses can have varied fronts, the industries most associated with commercial-front brothels include spa salons and massage parlors, bars, cantinas and clubs, which may be operated by small, mid-sized or large criminal networks.3
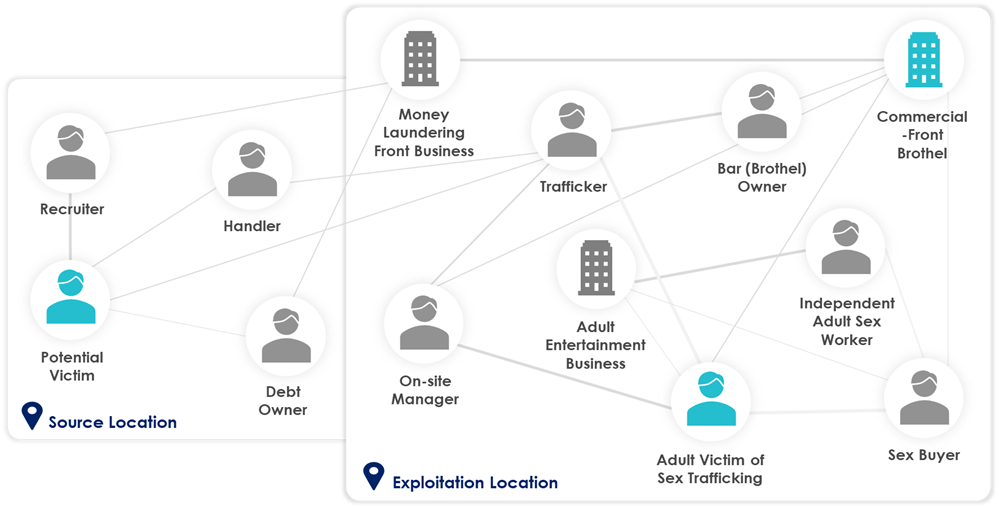
Graphic 1 shows how this model applies to identify and map the actors involved in the commercial-front brothel’s business model, where links between these actors represent the expected flows of money.
Graphic 1: Personas Involved in Commercial-Front Brothels
Source: RedCompass Labs
Visualization by Silvija Krupena
This model includes both victims and criminal actors, as well as potentially “innocent parties” that exhibit some criminal or victim behaviors (as discussed in the previous article, no one red flag in isolation can reveal HT). However, even without the network view, understanding the distinctive roles that individuals and organizations play in a given HT typology provides the starting point for effectively identifying behavioral red flags.
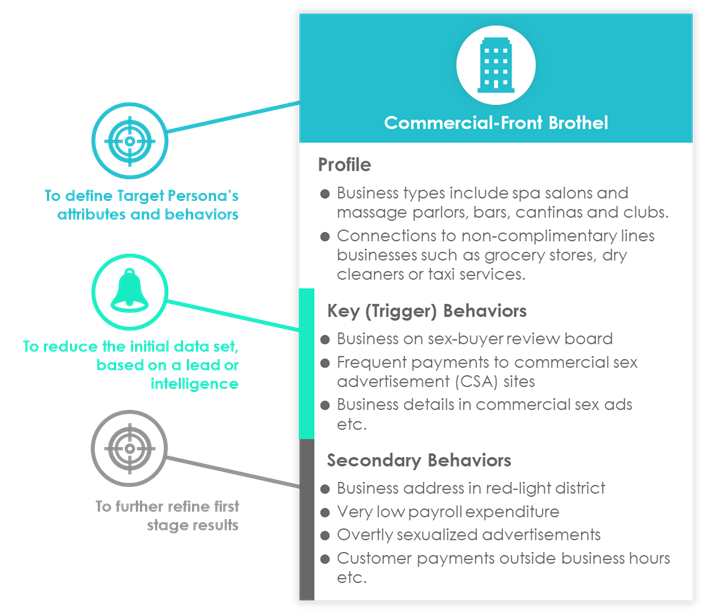
Based on your understanding of the selected HT business model and how it presents in your institution, your institution can start to build up persona profiles. Detailed profiles of target and alternate personas are based on their personal attributes, such as age, gender, income and location; as well as their business attributes, such as industry, activity and size, as well as key characteristics of the roles they play. However, just knowing the attributes is not enough; the context is essential.
In this example, target personas typically include the businesses matching the profile of a commercial-front brothel (as demonstrated in Graphic 2), the traffickers, the brothel owners or managers, the recruiters and the victims. These personas often work together in a complex network, with different individuals and organizations playing different roles at different stages of the trafficking process, and can also uncover (or go hand-in-hand with) other illegal activities, such as fraud, drug trafficking or money laundering. This map also covers alternate personas that may engage in similar behaviors but are not necessarily criminal, such as the adult entertainment businesses, the independent sex workers or the sex buyers, that can be removed from the results to reduce the noise.
Graphic 2: An Example of a Commercial-Front Brothel Persona
Source: RedCompass Labs
Visualization by Silvija Krupena
Step 3: Adopting Intelligence-led Detection
Once defined, models need to be applied, tested against the live data and refined depending on the results. Just as the real world and criminal behaviors evolve, so should the model, and emerging targeted intelligence, which is essential to ensure the dynamic reflection of the changing landscape of HT risks.
Sourcing and leveraging all available data, both internal and external, is a critical starting point and can determine the outcome of any detection model. Consolidating your data can yield greater context, meaning and understanding of customers and other parties, as well as their relationships, behaviors, and risks. By leveraging open-source intelligence (OSINT) and third-party sources, you can gain actionable intelligence. Examples of high-value external data sources in the context of the commercial-front brothel typology include:
- Social media—advertising, use of real or alternate names, contact information
- Adverse media—indicates potentially illicit activity
- Business websites—details of opening hours, overtly-sexualized content
- Business reviews—indicate suspicious activity related to commercial sex
- Court proceedings—high-quality name matching, alternates, address, age, associates
- Regional context—locations, naming conventions, keywords, preferred technologies as well as services, and others
Technology Considerations
When considering technology, there are considerable differences between rules-based and behavioral analytics based systems.
Rules-based technology uses a set of simple formula-based instructions to identify specific suspicious activities, by searching and flagging the transactions if they match the parameters of a particular rule. This technology cannot support a persona-based model as it generates separate alerts for the same customer with little to no context, significantly reducing operational efficiency and detection of real risks.
In comparison, behavioral analytics based technology moves beyond simple rules by adding fuzzy logic, machine learning, artificial intelligence (AI), and customer behavior and pattern recognition capabilities, allowing configuration of parameters that relate directly to the target persona behaviors.
Multiple industry reports4,5,6 in the market demonstrate that the best results can be achieved when the advanced behavioral analytics based technology is enhanced with entity resolution and network generation capabilities to effectively identify, visualize and resolve a range of complex HT-related suspicious activities.
However, it is worth noting that regardless of how advanced, clever and powerful the technology used is, it will not change the game unless the first and most critical step is addressed. Each bank must develop a deep understanding of its relevant, indiviual HT risks, vulnerabilities and threats, in order to be able to implement the most effective mitigation and detection controls.
Conclusion
The use of a persona-based approach in financial crime is a relatively new area of research and application, but it is already demonstrating the potential to significantly improve the understanding, detection and prevention of complex crimes such as HT. This innovative methodology, in combination with intelligence-led human trafficking detection, can close the gaps that allow criminals to use legitimate financial systems, often in plain sight – and thereby, breaking the HT business model and leading to a real-life reduction in harm, protection of victims and detention of perpetrators.
Silvija Krupena, CAMS, head of FIU, RedCompass Labs, [email protected], ![]()
- Silvija Krupena, “Human Trafficking: Persona-based Typologies and Methodology,” ACAMS Today, January 10, 2023, https://www.acamstoday.org/human-trafficking-persona-based-typologies-and-methodology/
- “How to Follow the Money of a Human Trafficker: US-Based Commercial Front Brothels,” RedCompass Labs, Polaris, October 2022, https://5522198.fs1.hubspotusercontent-na1.net/hubfs/5522198/%239001.pdf
- “The Typology of Modern Slavery: Defining Sex and Labor Trafficking in the United States,” Polaris, March 2017, https://polarisproject.org/wp-content/uploads/2019/09/Polaris-Typology-of-Modern-Slavery-1.pdf
- “AML/CFT Industry Partnership: Industry Perspectives – Adopting Data Analytics Methods for AML/CFT,” Monetary Authority of Singapore, November 2018, https://www.mas.gov.sg/-/media/MAS/Regulations-and-Financial-Stability/Industry-Perspectives–Adopting-Data-Analytics-Methods-for-AMLCFT.pdf
- “Leveraging innovation to fight trafficking in human beings: A comprehensive analysis of technology tools,” OSCE Office of the Special Representative and Co-ordinator for Combating Trafficking in Human Beings and Tech Against Trafficking, Vienna, May 2020, https://www.osce.org/files/f/documents/9/6/455206_1.pdf
- “Opportunities and Challenges of New Technologies for AML/CFT,” FATF 2021, Paris, France, https://www.fatf-gafi.org/publications/ fatfrecommendations/documents/opportunities-challenges-newtechnologies-aml-cft.html
Share this post